When selecting wireless modems, there’s a checklist of features to consider. We’ve presented those here.
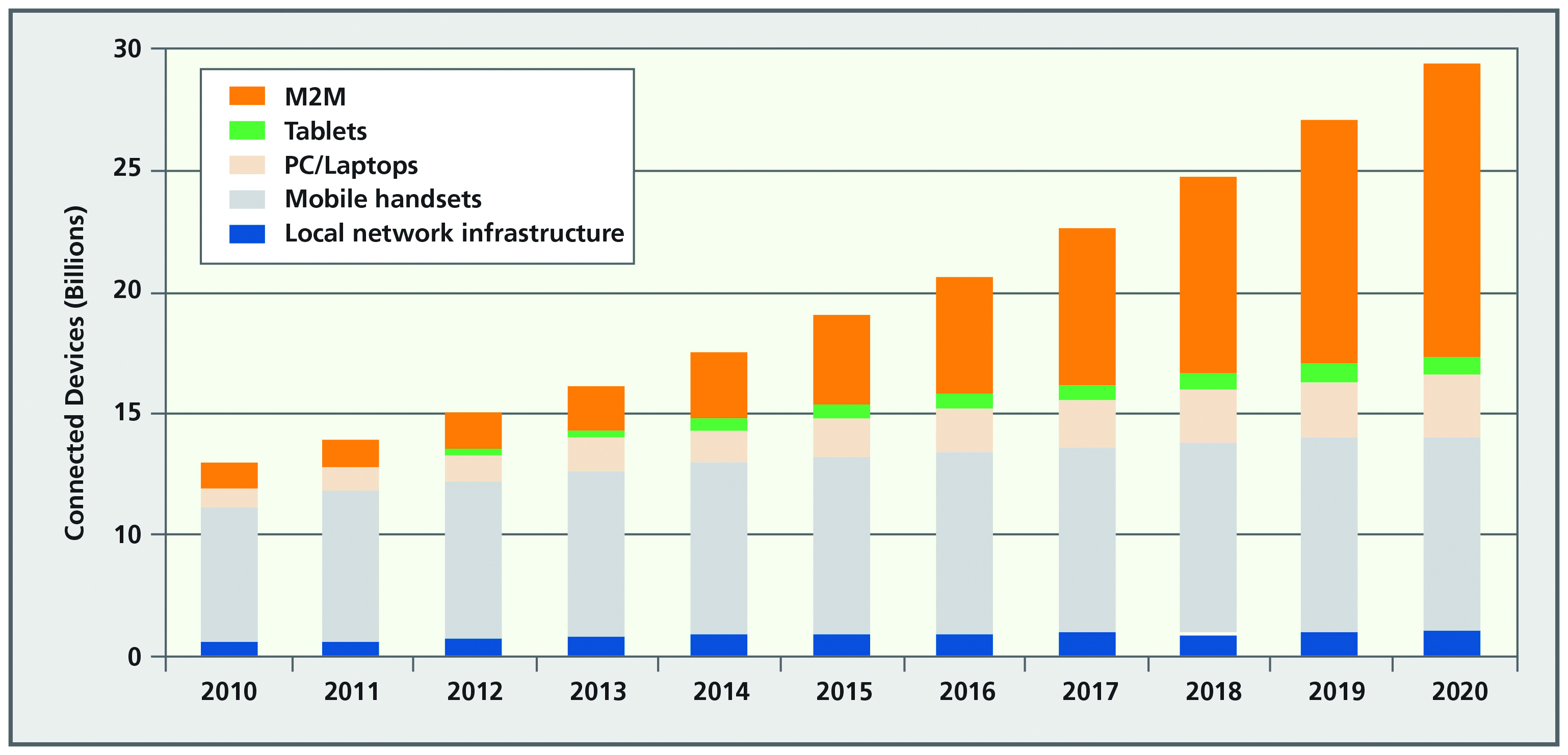
The growth rate of machine-to-machine (M2M) connections now far exceeds new connections between people, and soon there will be many more machines than people connecting over cellular Industrial computer networks, as shown in the GSM Association forecast in Figure 1. These in-vehicle system include security systems, meters, robots, vending stations, asset trackers, and emergency call systems. The variety is growing by the day, as are the silent conversations between millions of machines exchanging data 24 hours a day, 7 days a week, with no human intervention.
At the same time, it’s becoming cheaper and easier to connect to fleet management the Internet and even mass produced computing devices are able to gather and process ever-larger volumes of data. The one potential bottleneck to greater M2M connectivity, the fact that all 4 billion+ IP version 4 (IPv4) addresses are already allocated, has been removed with the introduction of embedded system. This supports 2128 addresses, more than enough for every grain of sand on Earth to have its own address. It’s perhaps no surprise then that LTE, the fourth generation of mobile networks (4G), is designed to deliver services such as data, voice, and video over IPv6.
To join the M2M in-vehicle system revolution, all that’s needed is to embed machines with small, economical (wireless) modems. Where location, speed, or navigation information needs to be established, the machines also need a GPS or GNSS (Global Navigation Satellite System) receiver. Both industrial computers, with an antenna, can fit easily in a device smaller than a mobile phone. GNSS is the standard generic term for satellite navigation systems that provide autonomous geo-spatial positioning with global coverage. It includes GPS (U.S.), GLONASS (Russia), Galileo (Europe), BeiDou (China), and other regional systems.
When thinking about how to equip an embedded system with communications capability, start by thinking about the needs of the application. Factors such as industrial computer longevity, geographical network coverage, or future-proofing to take account of future wireless network upgrades, are all important considerations. Here are some of the product features to consider when selecting wireless fleet management modems.
refer to:
http://embedded-computing.com/articles/the-fast-growing-m2m-market-presents-a-series-of-wireless-design-challenges/


